Security pride’ about the iPhone … However, there are many factors that threaten the iPhone ecosystem, and
there are many cases where privacy-infringing factors are automatically activated… Disabled by adjusting options
Dependence on smartphones It’s higher than ever From financial transactions to checking health status, contact with acquaintances, and consumption of various contents, we do everything through our smartphones. It was the iPhone that opened the smartphone era, and the iPhone remains the most popular smartphone to this day. But from a security standpoint, how secure is the iPhone?
Randy Pargman, former computer director for the FBI, said, “iPhone users are very confident about their equipment. Compared to Android, security is almost always first.” However, he points out, “We must not forget that much of that confidence in iOS is being overlooked, and that iOS is now more vulnerable than ever.” This weekend’s edition is dedicated to security tips for iPhone users (but most are also applicable to Android).
- Download and organize the app
There are probably a few things that you have installed in your phone right now but haven’t turned it on for quite some time. Not only do these apps unnecessarily eat up storage space, but they themselves pose a security threat. In particular, if the apps are abandoned by the developers, so security updates are not made, they can become an unnecessary attack path. So, if there are such apps, you need to delete them or update them. If the version is no longer being updated, it’s a good idea to find another app with similar features.
Security experts recommend that you only download apps from the App Store. They also say that we should do “smart shopping”. “Before installing an app, it’s a good idea to read user reviews thoroughly, and if you find anything suspicious, do some research with the developer and the app. A simple Google search will reveal what a particular app or developer is and whether it is safe to use.” Security analyst Jack Gold explains.
- Check regularly for app and iOS updates
When you ask experts for security tips, updates are the most common. Updating is the act of blocking publicly known vulnerabilities of hacking techniques. In other words, it is a way to defeat the hacker’s attack plan or increase the amount invested in the plan. So, the updates of apps and operating systems cannot be overemphasized. If it is difficult to check frequently, it is also a good idea to set all updates automatically.
Rick Holland, CISO at Digital Shadows, said, “The buy-once idea is in the minds of consumers. When possible, constant maintenance and management through updates is essential.” “Not just security updates, but feature updates as well. Many developers also include security updates in feature updates.” Fortunately, iOS updates are handled by Apple.
- Flashlight app asking for my location?
This is strange indeed, but it is also common. If you carefully read the permissions that apps require from users when installing, there are quite a few things that are difficult to understand. As in the sub-title above, it’s just an app that turns on a light, but there are quite a few apps that ask for access to location information, or even touch the microphone, camera, and contact information. Experts recommend that you review the permissions your app requires during installation, and see if it’s essential for your app to function.
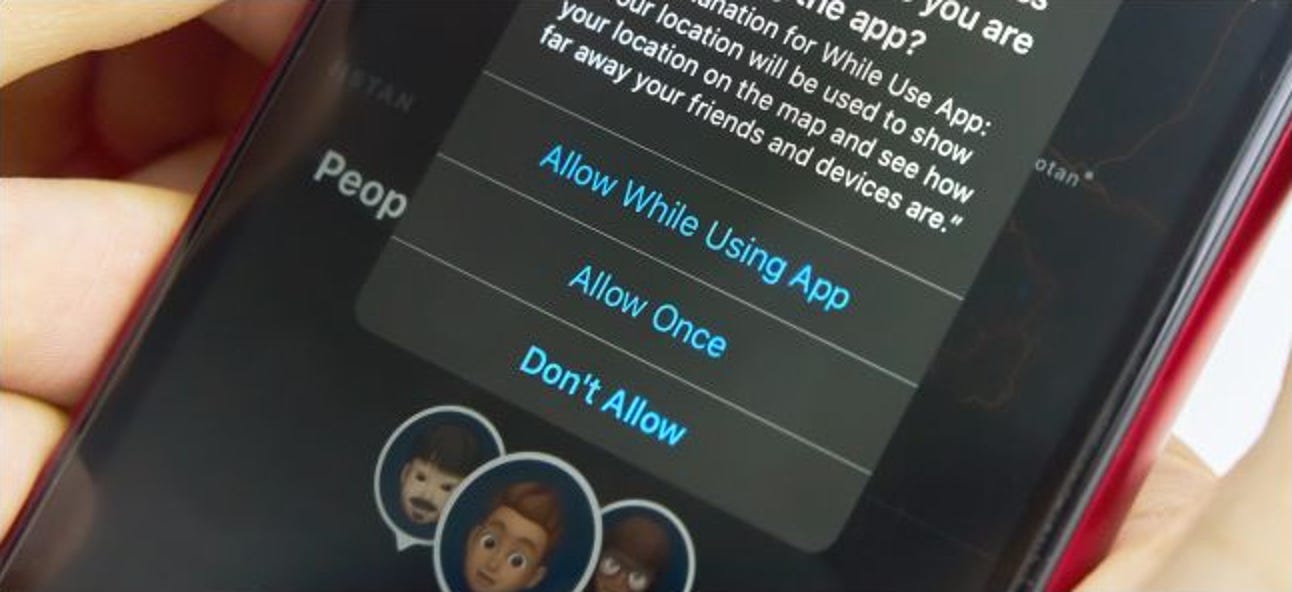
Open your iPhone’s settings window, go to the Privacy section, and you’ll see which apps are accessing your contacts, calendar, photos, Bluetooth, microphone, camera, health data, and more. Similarly, similar information can be found in the Location Services section. It is necessary to carefully review and adjust this list.
Privacy expert Attila Tomaschek explains: “Apps that have absolutely nothing to do with how they function and ask for unnecessary information, often in an attempt to monetize that information by selling it to third parties.” do. “Especially flashlight-related apps are notorious for this. Not all of them are like that.”
- Create a password by mixing numbers and letters.
By now, most iPhone users are probably familiar with biometric authentication. Even so, it is very important to set a secure password. “Even if you’re using fingerprint or facial recognition technology, the most important thing in the iPhone’s access control function is still the password or code,” says system engineer Ahmed Mohamed. He emphasized, “It is important to set a combination of numbers and alphabets.” “A basic four-digit number is not enough.”

“Enter the settings options and select ‘Touch ID & Passcode’ or ‘Face ID & Passcode’. Then select ‘Change Passcode’ and hit ‘Passcode Options’. You will then be able to select the ‘Custom Alphanumeric Code’ option. This allows you to set your passcode as a combination of numbers and alphabets. And do not share this password with anyone.”
- The more passwords, the stronger the security.
One of the things that security experts strongly recommend is multi-factor authentication. “A lot of people think biometrics are a substitute for passwords, but they’re wrong,” says Ken Underhill of Cybrary. “It’s more of a replacement for user ID. It does not replace passwords, nor should they be. Strong passwords are still essential for security. So instead of thinking of replacing it with biometric authentication, it is better to learn how to set up and manage strong passwords.”
It is in iCloud where passwords should shine particularly strong. It is a place where many iPhone users connect and store various data. “If you don’t know about other places, it is always recommended to apply multi-factor authentication to iCloud. It is also a good idea to set up a separate password for iCloud. That way, even if someone succeeds in hacking the iPhone, they lose access to valuable information.”
In fact, many iPhone security incidents start by stealing account passwords from iCloud, rather than directly penetrating iOS or apps. “You know that iPhone users have the same passwords for iCloud and their own iPhones. So, by attacking the cloud first, and accessing various data through it, it has an effect similar to hacking the iPhone. iCloud should be managed separately from the iPhone.”
“The richer the password, the better,” says Chris Hazelton, head of solutions at Lookout. “You have to use a lot of passwords to exhaust the attackers. Think of it as having to crack your password step by step. I’d rather go somewhere else. However, many passwords cannot be managed solely by memory. We recommend using a password management app.”
- Limit the number of Attempts
Attacker who succeeds in stealing an iPhone by limiting the number of logins will first attempt a brute force attack. It tries to log in until the password is unlocked. It is possible to limit the number of these attempts. Go to the Settings option, select ‘Touch ID and Passcode’, then scroll down to the bottom and change the ‘Erase Data’ section to On. In this case, the data on the phone will be erased when login attempts fail 10 times in a row. “Of course, this is a difficult option to use if you forget your login method (ie your password). Instead, if you regularly back up your data, it’s okay to forget about it.” Komashek’s explanation.
- Don’t Forget Safari and Ads Options
Some websites implement ‘cross-site tracking’ to keep an eye on users’ online activity patterns. This is to find out which places users mainly visit, and which services or products they are interested in, and then send advertisements accordingly. Apple has given iPhone users control over it.
If you go to Settings->Safari->Privacy & Security and turn on the ‘Prevent Cross-Site Tracking’ option, advertisers will not be able to access your browsing history. That doesn’t mean that the number of ads appearing on Safari is decreasing. Of course, this can also be adjusted by adjusting the options. In particular, you can disable pop-up ads or warn you about fake websites.
If you don’t want ads based on your interests to appear when viewing app stores and app news, you can adjust the options in ‘Settings -> Privacy -> Ads’. To disable location-based ads, go to ‘Settings -> Privacy -> Location Services -> System Services’ and turn off ‘Location-based Apple Ads’.
Safari, by default, uses the Google search engine, which you can change too. DuckDuckGo is famous as a search engine with strong privacy features. To set this, for example, you can change it by selecting the ‘Settings -> Safari -> Google’ option.
- 8. Beware of Click anything
Clicks It is now common knowledge not to click anything. That doesn’t mean we’re all good at it, but we all know it. Then the attackers are changing their tactics. Send a shortened URL or send a QR code through a mobile text message. Transmitting malicious links hidden in these two is a popular trend in the recent mobile environment.
“Phishing is the most common attack method in the current mobile environment,” Hazelton explains. “The most common hints in phishing texts and messages are grammatical errors, spelling errors, and crude design,” Hazelton said.
- Deleting tracking data from
Images Everyone has probably received a promotional or advertising email full of images at least once. However, there are pitfalls to these images. It may contain code for tracking purposes. This is because the company that sent the ad hides this to see if the email has been opened. However, there is no guarantee that these techniques will be used ‘only to check if an email has been opened’. There is a high possibility of abuse, and the moment it is abused, privacy is violated and the possibility of a security incident increases. That’s why it’s convenient to tinker with the tracking code embedded in these images.
“First of all, if you are a frequent e-mail user on your iPhone, you should adjust your e-mail options so that images are not automatically downloaded. If malicious images are downloaded incorrectly, sensitive information may be exposed.” Joseph Carson, CISO at Thycotic, explains: “In most cases, image download will be automatically enabled. It is recommended that the user manually navigate to the options and change them. This alone can significantly lower the risk.”
It’s also worth remembering that location data is automatically inserted into photos you take with your iPhone when the Camera app is set to access location information. So, keep this in mind when sending your photos somewhere. “When sharing photos, simply disable Location through the Options window.”
- Public Wi-Fi Is Never Safe
Security experts don’t like public Wi-Fi very much. Connecting itself doesn’t mean anything. There is a big risk in doing things that require confidentiality, such as making a shopping payment on public Wi-Fi, making a remittance, or logging in by entering a password.
Renee Tarun, CISO at Fortinet, said: “I don’t mean that all public Wi-Fi is a risk-prone space, but it’s not uncommon for an attack to disguise itself as a public Wi-Fi base station and wait for people to connect,” said Renee Tarun. It is true,” he warns. “If a victim connects to this fake base station and uses the Internet, the attacker can intercept a significant amount of data. As a user, the easiest thing to do is to turn off Wi-Fi auto-connect.”
What if you really need to connect to public Wi-Fi? Tarun recommends “using a VPN to connect”. “In that case, the VPN encrypts your traffic, making it difficult for criminals or trackers to access sensitive data.”

